Community Edition 21.0.3Released on April 19, 2021 (Milestones). | Enterprise Edition 21.0Released on March 8, 2020 |
Windows
Mac OS X
Linux
Eclipse Plugin
Note: plugin is compatible with Eclipse platform (from Neon to 2020-09). Required plugins: gef and draw2d. ChecksumsPrevious versions | Enterprise Edition features:
|
| Usually we release a new Minor Community Edition version once per two weeks. Major version is released quarterly (every 3 months). Information about previous releases you can find here. | |
Tested and verified for MS Windows, Linux and Mac OS X.
Install:
Windows installer – run installer executable. It will automatically upgrade version (if needed).
MacOS DMG – just run it and drag-n-drop DBeaver into Applications.
Debian package – run sudo dpkg -i dbeaver-<version>.deb. Then execute “dbeaver &”.
RPM package – run sudo rpm -ivh dbeaver-<version>.rpm. Then execute “dbeaver &”. Note: to upgrade use “-Uvh” parameter.
ZIP archive – extract archive and run “dbeaver” executable. Do not extract archive over previous version (remove previous version before install).
Upgrade – don’t be afraid to remove previous DBeaver version – your settings won’t be lost. All settings are kept in the separate folder (DBeaverData in user home)
Java notes:
DBeaver requires Java 11 or higher. Since version 7.3.1 all distributions include OpenJDK 11 bundle.
If you want to use you own locally installed Java you may delete folder “jre” in the DBeaver installation folder.
Debian repository:
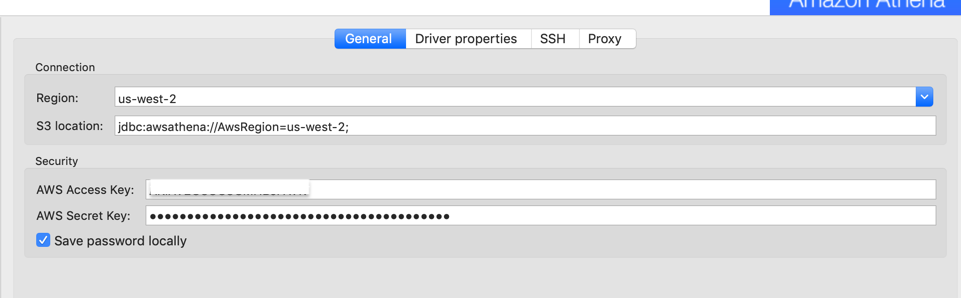
Product Overview CloudBeaver is a new universal interface for data management developed by the DBeaver team. CloudBeaver is especially adapted for AWS Cloud services. This is the light web-application that you can share among all AWS users within your company. Rapidly create and deploy powerful Java applications that integrate with live AWS Management data! Manage AWS Management data with visual tools in DBeaver like the query browser. The CData JDBC Driver for AWS Management implements JDBC standards that enable third-party tools to interoperate, from wizards in IDEs to business intelligence tools. Open the DBeaver application and, in the Databases menu, select the Driver Manager option. Click New to open the Create New Driver form. In the Driver Name box, enter a user-friendly name for the driver. To add the.jar, click Add File.

Ubuntu PPA:
You can use PPA repository to easily install/upgrade DBeaver on Debian Linuxes. Mostly it is the same as regular Debian repo but it is hosted on Launchpad.
Early Access:
You may get latest build (EA version) of DBeaver. Usually it contains all major bug fixes found in current stable version. Just choose the archive corresponding to your OS and hardware from the following folder: EA version downloads.
Source code:
Community Edition sources, issue tracker, older releases, etc: https://github.com/dbeaver/dbeaver
Archive:
All recent DBeaver versions are available in the archive.

CloudBeaver
DBeaver is desktop application.
If you are looking for a web-based database management system – please check another of our products: CloudBeaver.
It is also open-source and free.
When connecting to a DB from your machine it is tempting to hardcode credentials. However, as we arefinding, correctly securing your systems with SSO (combined with MFA) is no longer justbest practice, it is becoming mandatory.
In this post we will see how to configure the multi-platform DBeaver database tool to connect to AWS Redshift using a SAML-based SSO provider. I will use URLs that are similar to thosegenerated by Okta, but any SAML provider should operate the same way.
The login sequence
The authentication required for a JDBC connection is usually provided by environment variables,saved credentials in a file, or a UI window that is native to the application being used. The AWS JDBC driver, however, needs to challenge the user for an MFA token without having accessto the UI of the application it is embedded in. To overcome this problem the driver uses a clever solution.
- The user initiates the login sequence by using the driver to connect to Redshift.
- The AWS Redshift JDBC driver starts a server listening on a local port (7890 by default) and thenopens a browser window (pointing to the SSO service, eg Okta) so that the user can log in.
- When the user has logged in, the SSO service communicates with Redshift to generate temporarycredentials (and set any groups), then redirects the user’s browser to POST to a URL of the form
http://localhost:7890/redshift/, together with a largeSAMLResponsepayload. - The browser follows that redirect, and in doing so it sends that data to the local driver, which isstill listening on port 7890.
- The JDBC driver now has a set of temporary login credentials, and it uses them to connect to the Redshift cluster.
The fact that the driver needs to open a browser means that many traditional login scripts and appsdo not support the flow. DBeaver does not by default, but it can be achieved without much work.
Prerequisites
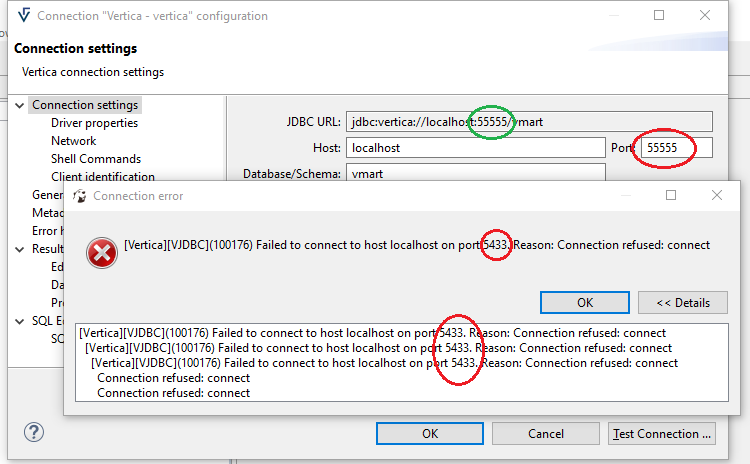
DBeaver does come with a “Redshift Driver” included, but it is not configured to allow SAML integration that requires a browser to open. Note, under the hood this does use the JDBC driver, but the UI presentedto you by DBeaver means it is not possible to configure for MFA flow.
Dbeaver Aws Iam
We need to create a new “Redshift (MFA) Driver” in DBeaver. To do that we must download the AWS Redshift JDBC driver with supporting libraries. You can find the JDBC Java libraries at this link.
Thus, you will need:
- The Redshift JDBC driver
- A running Redshift instance
- An Identity Provider (IdP) like Okta
- A configured SAML 2.0 application in that provider
Setting up the SSO Redshift application is beyond the scope of this article, but some pointerscan be found at the end of this post.
Configuring the connection
To create a new DBeaver Driver (using the AWS Redshift JDBC Driver):
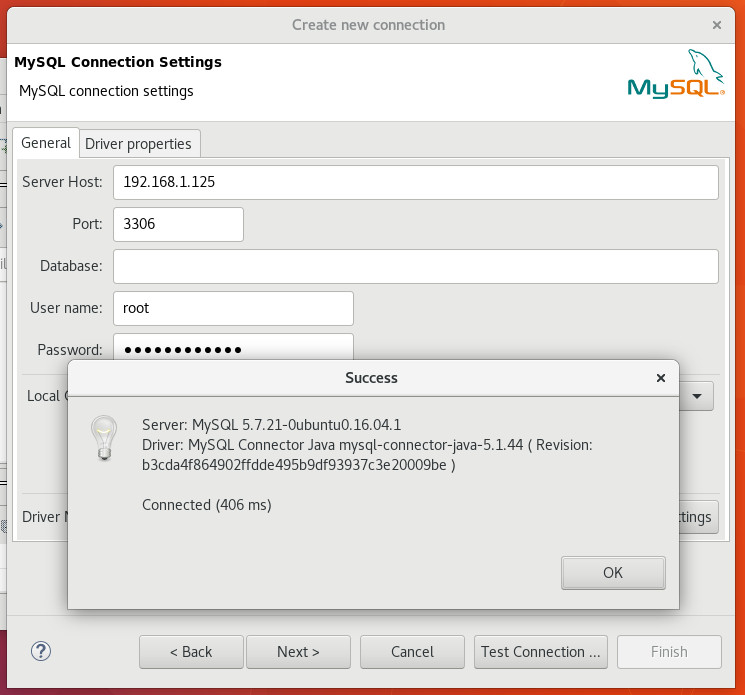
Dbeaver Aws Driver
Go to Database > Driver Manager
Search for “Redshift” then select it and click Copy
Fill out the form as below. The changes will be:
- Change the name to “Redshift (Okta MFA)” or similar
- Change the URL Template to:
In “Libraries”, choose “Add File” and add all the files from the downloaded AWS JDBC driver pack zip
- Press OK
To create a connection:
- Choose “Database” -> “New Database Connection”
Search for Okta (or the name used in step 3i), select it and hit “Next”
Fill in the hostname of your Redshift instance and the database to connect to. Leave the username and password as they are. They are ignored.
Configure it to use your pre-setup Okta app by clicking on the Driver Properties tab and adding a new property.To add a new property, click the tiny button with a green plus on it.The name of the new property is
login_url, and the value is the SAML target URL, which for Oktaends in/sso/saml.- Press OK
Finally, you can activate the connection. You will see a browser window open that will take you to Okta. If you are not yet logged in it will prompt you to do so, including MFA.
Once done, it will show the following message. You can close the browser window. You are connected.
That’s it!
You may find it is initially off-putting, the way a browser window suddenly opens when you log intoDBeaver, but the improvements in security are undeniable.
Overall we’ve been very happy with the new setup.
Good luck with your integration!
Appendix: Setting up an Okta Redshift application with MFA
As mentioned above, the full set of steps to set up an Okta connection to Redshift is beyond the scopeof this post, but here are a few pointers which may help:
- Do not use the Okta “pre-prepared” Redshift app. It is not configured to allow MFA connectivity.Instead, create a new (custom) “SAML 2.0 app”.
The main guide for how to set up the custom app is provided by AWS.
However, it has a few mistakes:
- The picture of the “Attribute Statements” shows a single “arn” on the right of the firstrow (in the Value column). It should be two arns, separated by a colon. The guidance text is correct though.
During the Okta setup at step 19 there is an example Group statement which is invalid. If it is not corrected then user groups do not get applied and the user cannot access any tables.
It says:
https://redshift.amazon.com/SAML/UnspecifiedAttributes/DbGroupsIt should be:
https://redshift.amazon.com/SAML/Attributes/DbGroups- The AWS SAML 2.0 provider setup forces the wrong “value” to
https://signin.aws.amazon.com/saml.It should behttp://localhost:7890/redshift. You can either choose “programmatic accessonly” or change the Trust Relationship Policy Document afterwards. It should look like this:
